In this article, we will share the features, working structure, and differences brought about by OPSWAT’s patented product Deep CDR (Content Disarm and Reconstruction), which pioneers the technology.
Challenges in Preventing Evolving Cyber Threats
Zero-day vulnerabilities and unknown malicious software complexities are increasing day by day. Zero-day malicious software is hidden within files by attackers and used in various attack vectors. Such attacks can easily bypass antivirus engines that detect known threats. Additionally, files cannot be definitively eliminated as attack vectors by ordinary sandbox solutions that only analyze files. Defense rates against malicious software with a single security perspective typically range from 40% to 80%. Moreover, during file transfer or in file storage areas, you may already have files with content that is not harmful but should not be present in the organization. In this case, you may want to perform security and content scanning or just reporting in real-time or at specific intervals to clean potential threats in file storage areas.
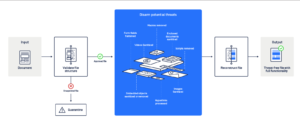
How Does Deep CDR Work?
- It evaluates and verifies the file type and consistency, and authenticates file extensions to prevent masking, notifying organizations if they are under attack.
- It separates files into components and removes potentially harmful or unwanted objects.
- It reconstructs usable files, retaining all file attributes and restructuring metadata.
- It compiles, renames, and delivers files while maintaining file structure integrity so that end users can safely use the file.
File Conversion and Restructuring
The customizable file conversion feature allows you to convert files to different formats (e.g., from a JPEG file to a Bitmap Graphics file, then to a PDF file, and back to JPEG). While files are being analyzed at the Deep CDR layer, potential threats within them utilize OPSWAT’s multiscanning feature that can be integrated into CDR. Through multiscanning, security is maximized by scanning with more than 30 different AV engines. If malicious content embedded in QR codes is detected, it is removed within seconds. Integrated with the MetaDefender Core platform through Deep CDR, you can perform file analysis in web traffic, email traffic, or cloud-local file storage areas.
It Analyzes over 150 File Types
Deep CDR recognizes over 150 file types to eliminate potential threats by restructuring files to be fully usable and secure. For example, when a “.docx” file containing a malicious URL enters your organization’s network through emails, file uploads, cloud applications, etc., it is scanned with multiple malware protection engines and inspected for potential threats such as OLE objects, bridges, scripts, etc. Then, depending on the Deep CDR configurations, all embedded threats are removed or sterilized as reconstructed. As shown in the output below, an OLE object has been removed and XML content has been sterilized.
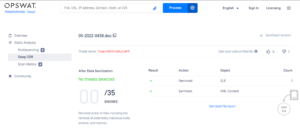
Supported file types include PDF, Microsoft Office, HTML, and many image files. Region-specific file formats such as “.JTD” and “.HWP” are also supported.
Why is Deep CDR Important?
Deep CDR has been developed with a 100% file security approach. Your organization’s files or file transfers are protected against both unknown malicious malware and zero-day attacks within the organization, ensuring control and security of sensitive data. Deep CDR also allows advanced reporting on reconstructed files through scanning, providing file-based comprehensive visibility. It guarantees the integrity of secure files during reconstruction, ensuring that files are not corrupted and are delivered to their source. It sterilizes by recognizing over 150 file types, eliminating possible embedded threats. Thus, there is no need to clean all file-based threats.
OPSWAT’s Deep CDR technology ensures the security of your incoming file traffic to your organization while also ensuring security in hosted files.
These technologies are available at OPSWAT, only at Secreto.