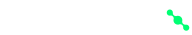In this article, we will evaluate email-related threats, the zero-trust security approach against these threats, attacks targeting email infrastructures, and defense methods against such attacks.
The Most Successful Type of Attack Used by Attackers
A significant portion of user-focused cyber attacks, which have the highest success rate in reaching targets, are carried out via email. Attackers often attempt to infiltrate organizations’ networks using various attack methods through this means. Phishing, identity theft, impersonation, and business email compromise attacks are commonly preferred methods. Malicious software takes advantage of various attachments, links in email content or headers, or files containing zero-day vulnerabilities when sent via email. Attackers may send emails disguised as a trusted source or conduct impersonation attacks that appear to be from within the company. As a result, users receiving the targeted email often do not question the content coming from a trusted source. The recipient of the targeted email can easily open a document sent via email, thereby allowing malicious software to infiltrate the company’s network.
Although such email-based attacks are attempted to be thwarted with various email security methods or user awareness notifications, attacks containing targeted malware that reach their target often result in negative consequences for organizations.
During 2023, a shocking 41% of security breaches were associated with identity theft. These attacks collect user credentials to gain unauthorized access to networks and access sensitive information. Typically, methods such as malware, phishing, and domain spoofing, which are a combination of identity theft, challenge traditional security protocols.
Zero Trust Approach to Email-Related Threats
The theft of credentials is only the first stage of potential cyber threats. These credentials serve as a key role for attackers to escalate their activities and lead to data breaches and threats that pave the way for more detailed cyber attacks.
Evolving email-based attacks, including credential harvesting, business email compromise (BEC), and the difficulty of emerging and email-borne new malicious software, necessitate the use of advanced email security solutions.
According to the latest data from 2023, email infrastructures were frequently targeted by threat actors. Research shows that 92% of successful attacks occur via email. These results highlight the importance of securing email infrastructures in 2024 and the necessity of adopting a zero-trust approach.
Traditional email security software evaluates email-based threats with a limited perspective. This limits defense against advanced and targeted threats to a minimal level. To defend against zero-day vulnerabilities, targeted attacks, or newly emerging vulnerability-focused malicious software, it is necessary to use advanced email security solutions.
Advanced Defense Method for Email Attacks
Ordinary email security software performs scanning with a single antivirus engine. Traditional analysis methods alongside email content sent with files can be easily bypassed by attackers.
OPSWAT Email Security solution, in addition to Anti-spam and Anti-phishing scans, scans files sent via email, documents in email content, and links for zero-day attacks using the Multiscanning feature with over 30 AV engines.
With its patented solution Deep CDR (Content Disarm & Reconstruction), it recognizes over 150 file types. It performs scanning on files, cleans unwanted objects within files according to defined rules to ensure full security of the files. It delivers the completely secure file it has created back to the source. It guarantees the integrity of the secure file after this analysis and reconstruction process.
It reveals unknown malicious software with Real-Time Next-Gen Sandbox, which works 10 times faster than traditional sandbox technology.
It decrypts password-protected archives sent via email and scans the files within. It detects security vulnerabilities through file-based vulnerability scanning. It scans hyperlinks found in email content, attachments, or subjects, or in QR codes. It detects and cleans harmful content and generates reports.
It utilizes the Proactive DLP feature to protect sensitive and confidential data. It can scan sensitive data in over 70 file types. It reorganizes sensitive data found in visual files with watermark and delivers them.
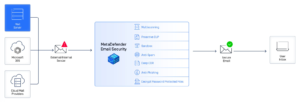
OPSWAT MetaDefender Email Security provides comprehensive security for email servers in on-premises or cloud environments. It offers easy integration with Microsoft 365 in the cloud. You can experience an advanced email security solution by experiencing the differences with traditional email solutions in a live environment.
OPSWAT Email Security solutions are available at Secreto. Contact Secreto to experience these advanced technologies.