OPSWAT
OPSWAT
OPSWAT is a pioneering cybersecurity company founded in the United States in 2000. Operating under the motto “Trust No File, Trust No Device,” OPSWAT aims to revolutionize the field of cybersecurity. This company takes a leading role in protecting critical infrastructures (Critical Infrastructure Protection – CIP), aiming to ensure the security of vital structures such as energy plants and water treatment facilities that directly impact human life. By combating malicious software and zero-day attacks, OPSWAT acknowledges the fact that every file and device has the potential to pose a threat.
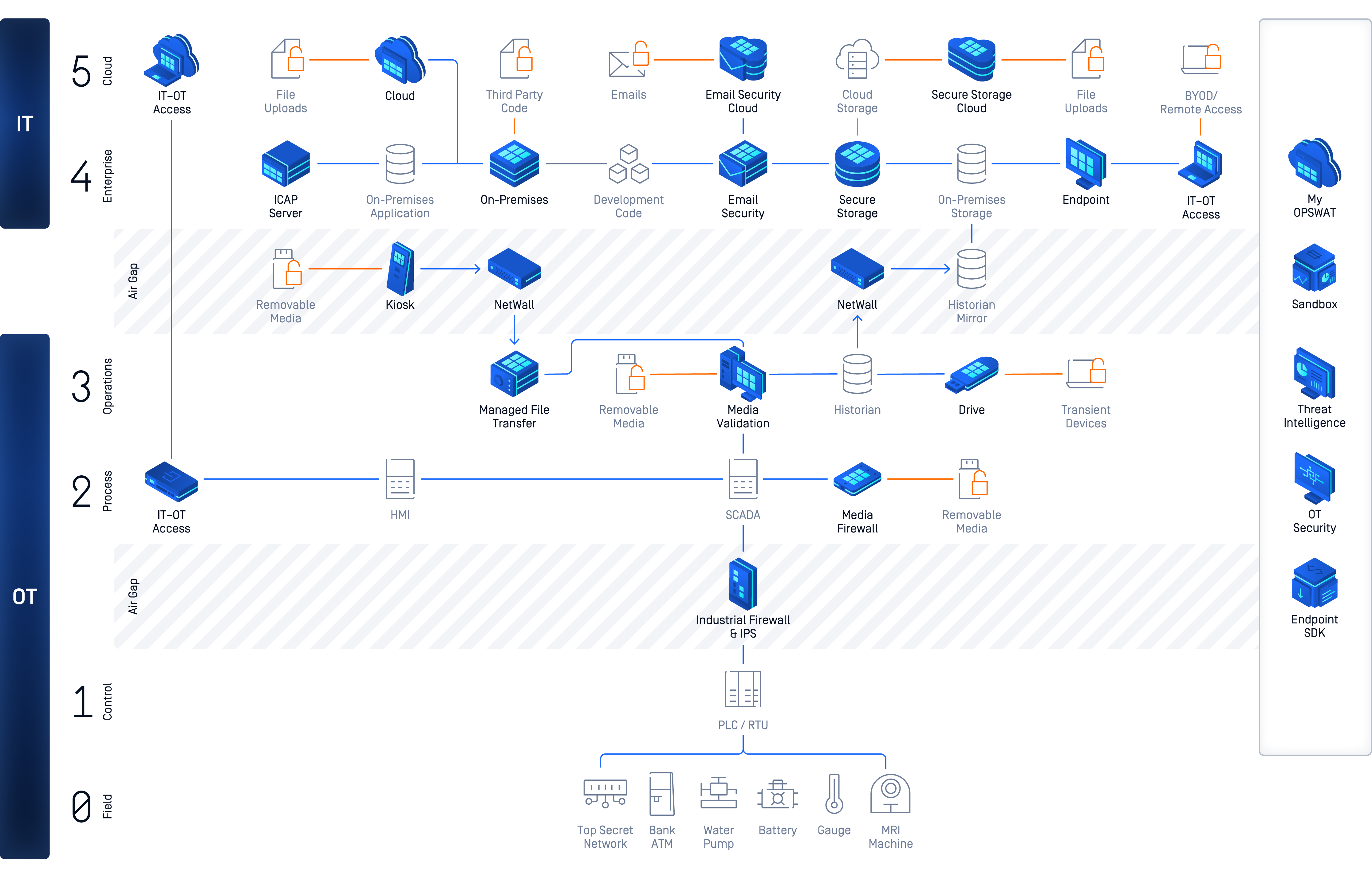
The solutions offered by OPSWAT span a wide range, covering both IT and OT infrastructures. Focusing on threat prevention and process development to ensure secure data transfer and device access, these solutions make the company unrivaled in the industry. Operating on the principle that threats must be addressed everywhere, at all times, OPSWAT offers unique technologies to protect organizations’ critical structures. Vital institutions such as 98% of the United States’ nuclear energy facilities rely on OPSWAT for their cybersecurity and compliance needs.
This unique approach and technological superiority have elevated OPSWAT from being just a cybersecurity company to a global leader in protecting critical infrastructures. Our collaboration with OPSWAT at SECRETO is a testament to our commitment to providing our customers with the most reliable and effective cybersecurity solutions.
OPSWAT’s advanced Email Security solution prevents phishing, Zero Day Malware, and unknown file-based exploit attacks from bypassing your organization’s email defenses.
Anti Phishing & Anti Spam ensures that your emails detect spam and phishing attacks with a rate of 99.98%, and URLs are rewritten through more than 30 sources to counter advanced social engineering.
Advanced Threat Protection (ATP): Opswat Email Gateway detects malicious software, phishing attempts, and other malicious content using advanced threat detection technologies.
Multi-Scanning Technology, scans emails with more than 30 antivirus engines, significantly increasing the detection rates of zero-day attacks and reducing the risk to almost zero.
Sandbox: MetaDefender Email Gateway Security, using the unique emulation engines of Metadefender Sandbox, can detect zero-day threats in various email attachments such as macros in MS Office documents or PDF files. Metadefender Sandbox technology is 10 times faster than traditional sandbox solutions.
Data Loss Prevention: Proactive DLP performs complete email content inspection, including checking more than 40 file types for compliance, while preventing the sending or editing of PII. It also utilizes Optical Character Recognition (OCR) technology to scan image files.
CDR (Content Disarm and Reconstruction): Deep CDR is OPSWAT’s advanced threat prevention technology that cleanses organizations of unknown and Zero Day vulnerabilities by purging more than 120 file types and emails of malicious active content. It employs advanced content sanitization and reconstruction techniques to eliminate potential threats in email attachments. Opswat CDR is 30 times faster than rival CDR solutions and 100 times faster than traditional sandbox solutions.
MetaDefender Core allows you to integrate advanced malware prevention and detection capabilities into your existing IT solutions and infrastructure to better address common attack vectors:
This enables you to protect web portals against malicious file upload attacks, enhance the effectiveness of your cybersecurity products, and improve your own malicious software analysis systems.
Scan. Sterilize. Deploy.
Easily integrate over 30 anti-malware engines into your workflow to scan files and detect known and unknown malware. Label and classify malicious files for further analysis and forensic purposes.
Identify suspicious files and potentially harmful files to prevent zero-day attacks and eliminate potential threats.
Automatically report and manage sensitive data in files to help prevent data loss.
Local integration with leading cloud providers (AWS, Azure, Google Cloud Platform) and on-premises storage solutions (Dell Isilon, NetApp SMB).
Cloud-Based Cybersecurity Platform
A comprehensive cybersecurity platform that provides detection, prevention, and threat intelligence technologies to protect organizations against file-based malware attacks. The MetaDefender Cloud API, which is easy to use and integrate, leverages advanced threat detection and prevention technologies.
Advanced Threat Prevention for Network Traffic
It is a plug-and-play malware prevention solution for network devices. It allows you to quickly expand MetaDefender’s advanced malware prevention technologies to your environment. It provides simple integration with any device featuring ICAP capabilities (Reverse and Forward Proxy / Web Application Firewall / Load Balancer / Firewall / Web Gateway / MFT)
The Secure Access module of the MetaDefender IT-OT Access Platform ensures secure access from the office, home, or other remote locations to your cloud and legacy applications while connecting from devices. There are two different methods available: Secure Cloud Access with SAML IdP Integration and Software Defined Perimeter (SDP) for zero-trust access control. Secure Access provides visibility and prevents unauthorized access.
You can ensure the security of external devices and OT assets with MetaDefender Drive.
When MD Drive is plugged into a USB port, the computer securely boots from MetaDefender Drive’s own operating system. This process allows for analysis without the need for software installation, scanning the entire device for malware and security vulnerabilities. Deep forensic analysis is conducted on every possible file, and detailed threat reports determine which files need to be removed or remediated.
OPSWAT MetaDefender Kiosk is your digital security guard
MetaDefender Kiosk ensures the secure transfer of files into the system by performing security scans on portable media coming from outside the OT Network. It is available in various hardware types to accommodate different use cases. MetaDefender Kiosk hardware scans over 20 types of portable media using Multiscanning technology, cleans potential indicators of attack in over 140 file types with CDR, and securely reconstructs files.
Top-Level Removable Media Security for Critical Systems
Verification of scanned portable media by KIOSK allows access. It connects to the USB port without requiring any software installation and prevents unprocessed or compromised files before they are used for SCADA/HMI.
Provides Cabinet-Level Security for OT Assets.
Acts as an OT Security Firewall. It behaves as an IDS/IPS. It learns, records, and when it detects anomalies, it blocks the traffic going to OT devices such as PLCs, RTUs, or HMIs operating at Layer 2.
It is an industrial security device and smart Intrusion Prevention System (IPS) positioned in front of industrial endpoints to protect critical PLCs, VFDs, DCSs, and other network-connected devices. It operates at Layer 2 and automatically learns and applies the normal operations of your facility environment, eliminating threats in real-time.
Security Gateway for IT/OT Convergence
Functions as a Secure Gateway (DataDiode). It ensures secure network segmentation with AirGap by providing one-way data flow.
Dealing with zero-day and unknown threats
It includes basic MFT features and the latest OPSWAT prevention technologies to provide secure file transfers, managed from low-security networks to high-security networks
Industrial Secure Remote Access Device
Most VPNs do not provide sufficient granularity to restrict remote user activity or enforce other security constraints after access has been granted. This exposes your OT environment to risk.
Secure Access for OT allows remote users to access only what they can see in their connections.
Secure Access for OT provides the most secure method for remote employees or third-party vendors to access OT endpoints
It monitors, reports, and provides protection by analyzing traffic for network and asset management in OT systems. It works in conjunction with the OT Firewall product. It continuously discovers threats, security vulnerabilities, supply chain breaches, and compliance issues, providing full visibility into your organization’s OT assets and networks.
Advanced Threat Prevention & Device Security Management Platform
My OPSWAT allows you to monitor and manage multiple MetaDefender products from a single location. From a central console, you can perform general tasks such as viewing managed anti-malware engines, managing virus definitions and engine updates, and checking license status
A powerful endpoint security software development platform, it is an interoperable, versatile, and modular framework that enables software engineers and technology vendors to create advanced endpoint security products.
The SDK reduces the time and effort required for integrators to develop functions for:
- Device Compatibility
- Vulnerability Assessment
- Patch Management
- Application Removal
- Removable Media Protection
- Anti-Keylogger
- Anti-Screen Capture
- Advanced Malware Detection
This feature, seamlessly integrated with my MetaDefender Cloud platform, enables you to effectively detect and capture emerging cyber threats using machine learning-supported Similarity Search, Pattern Search, and comprehensive Reputation Search APIs. It can quickly match complex patterns in known malicious files and identify zero-hour threats through more than 300 features
This feature, seamlessly integrated with my MetaDefender Cloud platform, enables you to effectively detect and capture emerging cyber threats using machine learning-supported Similarity Search, Pattern Search, and comprehensive Reputation Search APIs. It can quickly match complex patterns in known malicious files and identify zero-hour threats through more than 300 features
This feature, seamlessly integrated with my MetaDefender Cloud platform, enables you to effectively detect and capture emerging cyber threats using machine learning-supported Similarity Search, Pattern Search, and comprehensive Reputation Search APIs. It can quickly match complex patterns in known malicious files and identify zero-hour threats through more than 300 features
This feature, seamlessly integrated with my MetaDefender Cloud platform, enables you to effectively detect and capture emerging cyber threats using machine learning-supported Similarity Search, Pattern Search, and comprehensive Reputation Search APIs. It can quickly match complex patterns in known malicious files and identify zero-hour threats through more than 300 features