LogRhythm SIEM Alarm Management and Incident Response Process
Understanding SIEM & Alarms
Increasingly complex IT environments expose organizations to a myriad of threats that can jeopardize sensitive data, disrupt operations, and damage reputations. SIEM (Security Information and Event Management) solutions play a crucial role in helping organizations detect, respond to, and mitigate these threats.
LogRhythm SIEM serves as a central task force for organizations to collect, correlate, and analyze large volumes of log and event data generated in their IT infrastructures. By aggregating data from endpoints, servers, network devices, applications, cloud services, and other sources, LogRhythm provides comprehensive visibility into the security landscape. The platform’s advanced analytics, machine learning algorithms, artificial intelligence engine, enable it to detect anomalies, identify patterns indicative of potential threats, and generate real-time alarms.
The LogRhythm NextGen SIEM solution offers robust capabilities for alarm management, enabling organizations to effectively monitor their environments and respond to security incidents in real-time.
Instant Alarm Management for Critical Events
An alarm is a record of an event or series of events that triggers an alarm rule.
Alarms don’t always occur at the most convenient times. When you receive an alarm, you might be dealing with different hazards, be at lunch, or be off-duty early in the morning. Wherever you are, you need to quickly assess the severity of the alarm to understand and respond to it. The best way to make this determination is when you have the relevant information. The faster an organization can act to prevent a threat from compromising critical data or causing serious damage, the more critical it becomes.
LogRhythm SIEM uses a combination of predefined correlation rules, behavioral analytics, and threat intelligence to generate alarms for suspicious activities. These alarms are prioritized based on the risk level they pose to the organization, allowing security analysts to focus their attention on the most critical alerts.
LogRhythm provides IT administrators with various predefined rules they can upload via the Knowledge Base. Alarm rules are configured and managed in the Client Console.
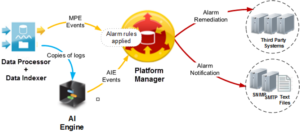
In LogRhythm, alarms can be triggered as follows
- The Data Processor receives logs from Agents. The log processing engine, known as the Message Processing Engine (MPE), then processes the log data and classifies a subset of it as MPE events.
- The Data Processor forwards MPE events to the Platform Manager. If LogRhythm is deployed with an Artificial Intelligence (AI) Engine, the Data Processor can also send copies of logs to the AI Engine for additional analysis. The AI Engine evaluates the logs based on AIE Correlation Rules. If a log triggers an AIE Rule, the AI Engine sends an AIE event to the Platform Manager (Alarm rules are already applied).
- As events are moved to the Platform Manager, the integrated Alarm and Response Manager (ARM) applies alarm rules to the live stream of event data. If an Alarm rule matches an event, an alarm is generated.
Alarms can trigger one or both of the following actions
- Notification: Alerts are sent to administrators via SNMP trap, email (SMTP), or text files.
- SmartResponse: An automatic script responds with an action to resolve the issue.
LogRhythm alarm rules monitor specific conditions such as network attacks, compliance issues, system errors, etc. For example, if log data reveals an attempt by a Trojan to enter the network, an alarm rule such as “Malware Alarm” is triggered, alerting administrators. Additionally, the alarm rule can trigger SmartResponse actions such as disabling an Active Directory account or killing a running process.
Incident Response Process (SmartResponse)
LogRhythm SIEM can automate response actions to security incidents in real-time. These actions may include blocking malicious IP addresses, quarantining infected endpoints, or triggering incident response workflows.
SmartResponse actions are automatic defense or operational responses given to triggered alarm rules. Below are some examples of the different functions that SmartResponse actions can perform:
- GWhen compromised systems are detected, SmartResponse actions can conduct vulnerability scans or packet captures on target hosts.
- SmartResponse actions can terminate inappropriate processes (such as BitTorrent or a P2P application) detected on a server.
- In the event of simultaneous successful logins to the same account from two different countries, SmartResponse actions can disable the account.
- When LogRhythm detects critical process issues, SmartResponse actions can automatically set network devices to debug-level logging.
An alarm rule can be configured to trigger up to 10 SmartResponse actions when activated. Actions can be executed immediately or after a core approval process. During the core approval process, individuals or groups must approve the action before it is executed (up to three approval levels can be configured). If multiple individuals are assigned to the same level, only one person needs to approve or deny the action.
In conclusion, LogRhythm SIEM provides powerful capabilities for alarm management, enabling organizations to proactively identify and respond to security threats. Leveraging advanced analytics, customizable alerts, and automated response actions, LogRhythm empowers security teams to stay one step ahead of evolving cyber threats and protect critical assets. As the frequency and complexity of cyber attacks continue to rise, investing in advanced solutions like LogRhythm NextGen SIEM is crucial to establish a strong security posture.